Digital Video Content Protection: Advanced Technologies Preventing Piracy During Transmission
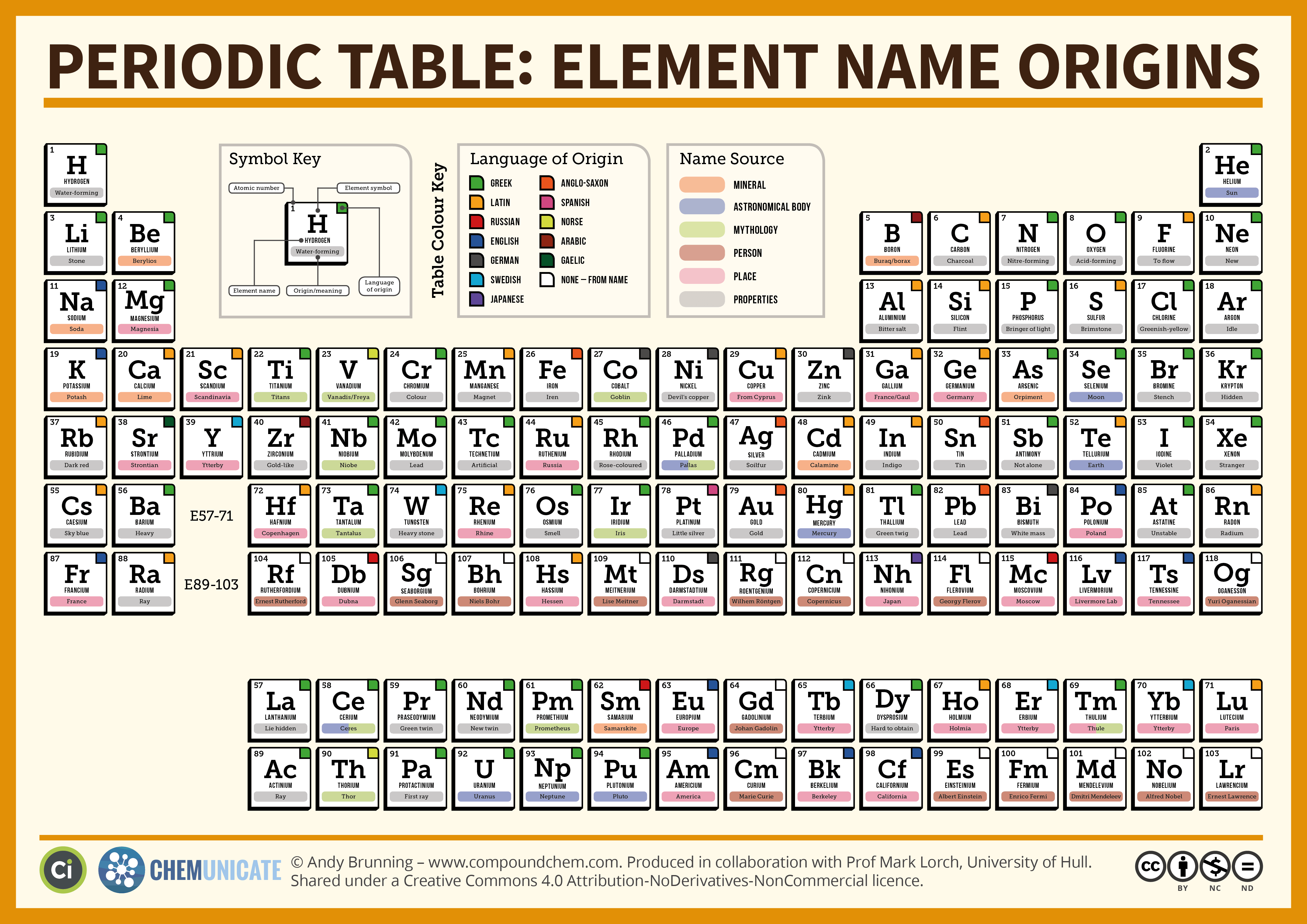
Understand digital video content protection
Digital video content protection represent a critical battleground in the entertainment industry. As streaming services and digital distribution platforms have revolutionized how we consume media, the need for robust security measures has become paramount. These technologies work wordlessly in the background, ensure that premium content reach legitimate viewers while prevent unauthorized access and distribution.
The foundation of digital video protection lie in sophisticated encryption algorithms and multi layered security protocols. These systems create an invisible shield around valuable content, make it most impossible for pirates to intercept and redistribute material during transmission.
Digital rights management (dDRM)systems
Digital rights management stand as the cornerstone of content protection technology. DRM systems create a secure environment where content owners maintain complete control over their intellectual property throughout the distribution chain.
Wide vineDRMm technology
Google’s wide vine represent one of the virtually wide adoptDRMm solutions in the industry. This technology employ hardware base security feature to create multiple levels of protection. The system operate through three security levels, with level 1 offer the highest protection by utilize hardware security modules within devices.
Wide vine’s strength lie in its ability to adapt to different device capabilities while maintain consistent security standards. The technology integrate seamlessly with content delivery networks, ensure that encrypt content remains protect from the moment itleavese the server until it reach the viewer’s screen.
Play ready protection platform
Microsoft’s play ready technology provide comprehensive content protection across multiple platforms and devices. This system excels in enterprise environments and support a wide range of content formats and delivery methods.
Play ready’s architecture include advanced key management systems that generate unique decryption keys for each view session. These keys expire mechanically, prevent long term unauthorized access still if security is temporarilycompromisede.
Airplay streaming
Apple’s airplay technology focus specifically on http llive-streaming((lHLS)ontent protection. This system integrate profoundly with appAppleecosystem, provide seamless security for iosiOSd macmacOSvices while maintain high quality viewing experiences.
Airplay’s implementation include sophisticated certificate base authentication systems that verify both the content and the request device before allow access. This dual verification create multiple barriers against unauthorized access attempts.
Advanced encryption standards
Modern content protection rely intemperately on military grade encryption algorithms that make intercept data well-nigh useless without proper decryption keys.
AES encryption implementation
Advanced encryption standard (aeye) form the backbone of most digital video protection systems. AAES128 and aeyes256 encryption provide different levels of security, with eyes 256 offer most unbreakable protection for thewell-nighh valuable content.
The implementation of eyes in video streaming involve encrypt individual video segments kinda than entire files. This approach allow for efficient streaming while maintain security, as each segment require separate decryption keys that expire rapidly.
Dynamic key rotation
Advanced protection systems employ dynamic key rotation to prevent long term security breaches. These systems generate new encryption keys at regular intervals, sometimes arsenic oftentimes as every few seconds during content transmission.
Key rotation ensure that flush if pirates manage to obtain decryption keys, their usefulness expires speedily. This approach create a moving target that make systematic piracy highly difficult and resource intensive.
Watermarking and forensic technologies
Beyond prevent initial piracy attempts, modern protection systems include forensic capabilities that help identify and track unauthorized distribution.
Digital watermarking
Digital watermarks embed invisible identify information straightaway into video content. These marks survive various forms of processing and compression, make them valuable tools for track pirate content support to its source.
Modern watermarking technologies can embed multiple layers of information, include viewer identification, session details, and distribution chain markers. This information become crucial evidence in legal proceedings against pirates.
Forensic watermarking
Forensic watermarking represent the virtually advanced form of content tracking technology. These systems create unique watermarks for each individual viewing session, allow content owners to identify precisely when and where security breaches occur.
The technology operate by make imperceptible changes to video frames that create a unique fingerprint for each stream. These fingerprints survive various forms of recording and re encoding, make them extremely effective for identify piracy sources.
Hardware base security solutions
The virtually robust content protection systems leverage specialized hardware components that provide security at the silicon level.
Trust execution environments
Trust execution environments (tees )create secure processing areas within devices where sensitive operations like content decryption can occur safely. These environments remain isolated from the main operating system, prevent malware and hack attempts from access decryption processes.
Tee implementation vary across different device manufacturers, but the core principle remains consistent: critical security operations occur in protect hardware that can not be access through software exploits.
Hardware security modules
Dedicated hardware security modules (hSMS))rovide the highest level of content protection by handle all cryptographic operations in specialized, tamper resistant hardware. These modules can detect physical intrusion attempts and mechanically destroy encryption keys if comcompromised
SMS are specially valuable in professional broadcasting environments where content value justify significant security investments. These systems provide audit trails and compliance features require by major content distributors.
Multi CDN protection strategies
Content delivery networks play a crucial role in content protection by implement security measures at the network infrastructure level.
Geo-block and access controls
Advanced CDN systems implement sophisticated geo-block technologies that restrict content access base on geographical location, device type, and user authentication status. These systems can make real time decisions about content delivery base on multiple security factors.
Modern geo-blocking go beyond simple IP address filtering to include device fingerprinting, behavioral analysis, and pattern recognition that can identify suspicious access attempts.
Token base authentication
CDN level token authentication create time limit access credentials that must be refreshed regularly throughout view sessions. These tokens include encrypt information about the authorize viewer, content permissions, and session parameters.
Token expiration and refresh mechanisms ensure that interrupted sessions can not be resumed without proper re authentication, prevent unauthorized access through session hijacking or credential theft.
Adaptive streaming security
Modern streaming protocols incorporate security measures instantly into their adaptive bitrate algorithm.
Encrypted media extensions
Encrypted media extensions (eEME)provide standardized interfaces between web browsers and drDRMystems. This technology enable secure content playback in web browsers while maintain compatibility across different platforms and devices.
EME implementation ensure that decryption keys ne’er become accessible to web applications or browser extensions, maintain security eventide in potentially compromise browse environments.
Secure media path
Secure media paths create protect channels for content transmission from decryption hardware through display systems. These paths prevent content interception at any point in the playback chain, include protection against screen recording and HDMI capture attempts.

Source: bernardmarr.com
Implementation of secure media paths require coordination between multiple system components, include graphics processors, display drivers, and output hardware.

Source: fity.club
Machine learning and AI power protection
Artificial intelligence technologies are progressively important in detect and prevent sophisticated piracy attempts.
Behavioral analysis systems
Ai power behavioral analysis can identify unusual access patterns that may indicate piracy attempts. These systems learn normal view behaviors and flag anomalies such as rapid content switch, unusual geographic access patterns, or simultaneous access from multiple locations.
Machine learning algorithms unceasingly improve their detection capabilities by analyze successful and attempt security breaches, create progressively sophisticated protection profiles.
Real time threat detection
Advanced protection systems employ real time threat detection that can identify and respond to piracy attempts as they occur. These systems can mechanically adjust security levels, revoke access credentials, or implement additional verification steps when suspicious activity is detected.
Real time detection capabilities include monitor for unauthorized screen recording software, suspicious network traffic patterns, and attempt to circumvent geo-block or device restrictions.
Future developments in content protection
The content protection landscape continue to evolve as new technologies emerge and piracy methods become more sophisticated.
Blockchain base rights management
Blockchain technology offer potential solutions for creating immutable records of content rights and distribution permissions. These systems could provide transparenttamperproofof tracking of content licensing and distribution chains.
Blockchain implementation in content protection could enable automate rights enforcement and provide clear audit trails for content usage across multiple platforms and distributors.
Quantum resistant encryption
As quantum computing capabilities advance, current encryption methods may become vulnerable to new forms of attack. Content protection systems are begun to will incorporate quantum resistant encryption algorithms that will remain secure yet against quantum computer will base attacks.
The transition to quantum resistant encryption represent a significant undertaking that require coordination across the entire content distribution ecosystem, from production studios to end user devices.
Implementation challenges and solutions
Deploy comprehensive content protection systems involve balance security requirements with user experience and technical performance considerations.
Performance optimization
Advanced encryption and security measures can impact streaming performance if not decently implement. Modern protection systems employ hardware acceleration and optimize algorithms to minimize performance smash while maintain security effectiveness.
Performance optimization include efficient key management, streamlined authentication processes, and intelligent caching of security credentials to reduce latency and improve user experience.
Cross-platform compatibility
Content protection systems must work seamlessly across diverse device ecosystems, from smartphones and tablets to smart TVs and gaming consoles. This requirement drive the development of standardized security protocols and universal DRM solutions.
Achieve cross-platform compatibility while maintain security require careful attention to the lowest common denominator of security capabilities across all support devices.
The ongoing evolution of digital video content protection reflect the critical importance of intellectual property security in the modern entertainment industry. These sophisticated technologies work unitedly to create multiple layers of protection that make piracy progressively difficult and economically unviable. As streaming will continue to will dominate content distribution, these protection systems will doubtlessly will continue will advance to meet new challenges and threats.
MORE FROM lowcostbotox.com